Published
Weekend Reading — The Churn
Design Objective
4 ways I’ve fucked up as a designer Solid takeaways, like this one:
Don’t skip process. User flows? User scenarios? User stories? User jokes? User lollipops and user flashlights and user sinuses? Yes please, give it all to me. I don’t care if it exists or not, I’ll learn it and I’ll find a way to apply it. Because these processes exist for a reason.
Tools of the Trade
FallibleInc/security-guide-for-developers To start with, a security checklist, and stats about vulnerabilities.
Accessible UI Components For The Web If a custom UI component must you build:
Custom UI components (with the exception of components that extend native elements like
<button>) do not have any built-in functionality, including accessibility, so this needs to be provided by you. ... The following is a list of questions you can ask yourself when attempting to make your UI components more accessible.
vfaronov/httpolice Lint for HTTP.
tfw you spend an hour banging your head against something because the way you configure it is a double negative
Lingua Scripta
Why object literals in JavaScript are cool Goes into all the things ES6 object literals that were not possible with ES5.
Lines of Code
I’ve noticed a “code smell” in object-oriented code that I call “Message Obsession”. I find Message Obsession causes similar difficulties to Primitive Obsession. However, Message Obsession appears to be the complete opposite of Primitive Obsession. Refactoring to address the difficulties caused by either Primitive Obsession or Message Obsession leads to the same design
“So you spent all day writing this tiny amount of code?”
“No I spent all day thinking about *how* to write this tiny amount of code.”
I think the biggest takeaway from my 16 years of programming is just 5 simple words:
Don’t try to be clever.
it("Should do that thing we talked about")
Architectural
The Churn What really happens when developers are constantly chasing the next big thing:
I understand. But that's because we got used to all that early rapid growth. Those were heady days; and we want them back again. But they're gone; and we have to face the fact that we are wasting time and effort on a massive scale trying to recreate them.
Why Uber engineering switched from Postgres To MySql Churn? Just guessing, because of this presentation by the same author, two years earlier, titled "Migrating Uber from MySQL to PostgreSQL".
Goodbye, Object Oriented Programming Highlights the false promises OOP made that didn't live up to the hype. But you can also read this as "things OOP doesn't do right, ignore those and only use the less clever OOP features."
Devoops
only two more days until Monday
Locked Doors
Pregnancy-tracking app was riddled with vulnerabilities, exposing extremely sensitive personal information The "fix it later" security culture at startups:
The companies backed by data-hungry VCs will perforce design their products to extract as much data as possible from their users ...
every dollar they spend on security engineering is a dollar they can't spend keeping the lights on while they try to raise another round, or attain profitability, or sell the company ...
If they do manage to survive their six-month timeline, they can fix it then (or maybe fob the problem off on some googleish giant that's acquired them).
NIST declares the age of SMS-based 2-factor authentication over It's about time. The second factor should be something you have. SMS is not something you have, it's something the carriers let you use.
New attack bypasses HTTPS protection on Macs, Windows, and Linux Always VPN on networks you do not control:
The attack can be carried out by operators of just about any type of network, including public Wi-Fi networks, which arguably are the places where Web surfers need HTTPS the most. It works by abusing a feature known as WPAD—short for Web Proxy Autodisovery—in a way that exposes certain browser requests to attacker-controlled code.
Delilah, the first Trojan to recruit Insiders Infosec has a new problem on its hands: a malware that extorts victims into stealing insider data.
Twas the week before DefCon, when all through the IRCs, red teamers were buying burner phones as if someone would blow a $1m iOS vuln on 'em
None of the Above
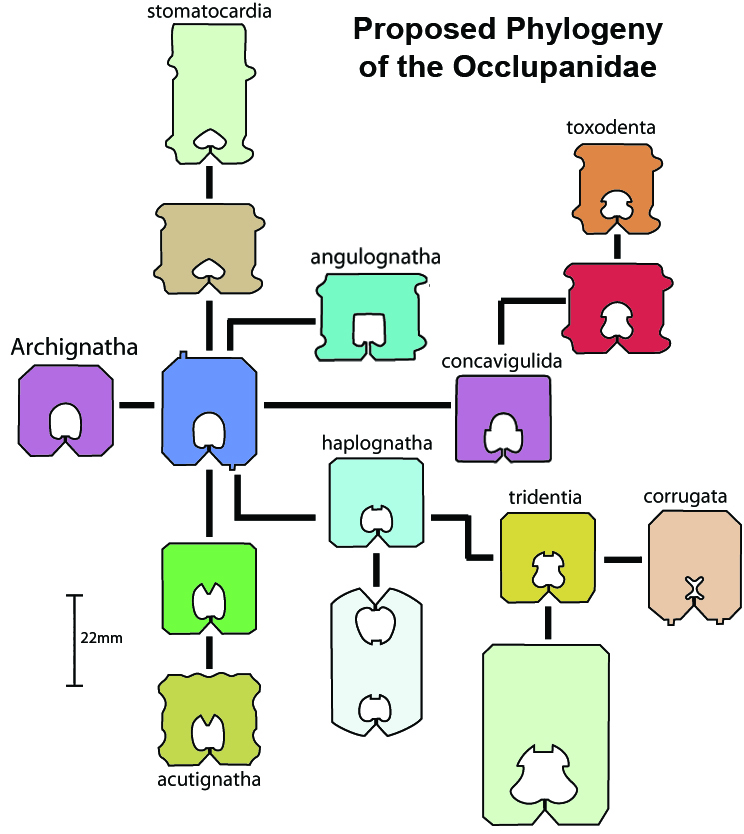
Taxonomy of the Occlupanida A taxonomy of plastic bread closures (Occlu=to close, pan= bread).
you may not think your brain is a supervillain. but 1) its called Brain and 2) it lives in a skull fortress
This race must be familiar for many women: she’s overqualified for the promotion, he’s unqualified, and yet it’s still a contest.
On a technicality Pretty much:
So I concluded that, for a smaller community, the people who need the rules are likely to be people who you don’t want around in the first place. And “don’t be a dick” covers that just as well.
Did Wes Anderson design North Korea? You decide

